IT Security Brief: Zip and Mov Domains

In May 2023, Google introduced eight new top-level domains (TLDs), including .zip and .mov. A TLD is the part of a website address that comes after the dot, such as .com, .org, or .ca.
ZIP and MOV Domains can be exploited by cyber criminals
The new .zip and .mov TLDs are being targeted by malicious actors to create deceptive phishing links. These TLDs are associated with common file extensions, making them attractive for exploitation.
Consider the following example to help understand the issue:
LEGITIMATE LINK: https://github.com/kubernetes/kubernetes/archive/refs/tags/v1.27.1.zip
This is a genuine link to a Zip archive hosted on GitHub, functioning as expected.
DECEPTIVE LINK: https://github.com/kubernetes/kubernetes/archive/refs/tags/@v1271.zip
This altered link would not link to GitHub, a trusted website. Instead, it would redirect the user to https[:]//v1271[.]zip, which could be a malicious website using the new .zip domain.
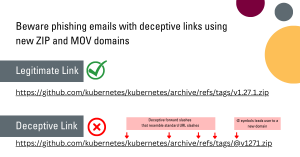
In this example, the deceptive link exploits two factors:
- The @ symbol redirects the user to a new domain. The content before the @ symbol in a standard URL is treated as user info, while everything after the @ symbol is considered the hostname. For example, the URL “https://google.com/gmail/inbox@bing.com” would redirect the user to bing.com instead of google.com.
- Bad actors can use different kinds of forward slash characters (/) that resemble standard forward slashes in a legitimate URL. Notice how the slashes look slightly different in the deceptive link above? This can trick the user into thinking they are clicking on a standard URL.
What should you do?
Please remain cautious and exercise good judgment when encountering unfamiliar or suspicious links, particularly those involving the .zip or .mov domains.
Additionally, take proactive measures to enhance your security, including:
- Keep your devices and software up to date.
- Use reputable antivirus software.
- Practice safe browsing habits.
If you do fall victim to a phishing scam, do not be embarrassed. Report any and all suspicious email messages to is-spam@mcmaster.ca. If you have opened any suspicious emails, links or attachments please report it to the UTS Service Desk.
You can also visit McMaster’s Phish Bowl to check out examples of recent phishing attempts reported by members of the McMaster Community.
Thank you for continuing to help McMaster stay cyber secure.
News CategoryRelated News
News Listing

Innovation Meets Leadership: McMaster and Cisco Spotlight Women’s Health and Technology
News Category
November 6, 2025

October 1, 2025

